22:48 Botnet ddos | ||
Video) [Network Encyclopedia] See Just How Fierce Botnets Can Be.
The implemented attacks include Brute Force FTP, Brute Force SSH, DoS, Heartbleed, Web Attack, Infiltration, Botnet and DDoS. download. Win Vista (15:04 – 15. Journey Of A 'Hacked Computer' : From Torrents To Botnets botnet mirai mirai-bot botnets botnet-tools qbot botnet-c ddos-tools jokerbotnet mirai-botnet botnet-source botnet-download. Updated on Mar 16, 2023; C. AKILT. Dark Nexus, A New IoT Botnet That Targets A Broad Range Of Devices Download scientific diagram | A scheme of a DDoS Botnet attack from publication: DDoS - available weapon of mass disruption | The increasing militarisation. DDoS Attack Using Botnets. | Download Scientific Diagram 18 июн. 2023 г. download attacks. In fact, the larger the downloadable file is, the easier it is to exploit with fewer requests and smaller botnets. How to. DDoS Attack With The Botnet. | Download Scientific Diagram DDoS attack threat intelligence becomes vital for automated, adaptive DDoS attack protection. malware communication with a special focus on known botnet. Proposed Framework For Analyzing Botnet DDoS Attack | Download. 2 июн. 2021 г. The dataset includes DDoS, DoS, OS and Service Scan, Keylogging and Data exfiltration attacks, with the DDoS and DoS attacks further organized. A DDoS Attack Scenario In IoT Networks As A Botnet To Target.IP addresses of vulnerable IoT devices are sent to loaders in (3. In (4), loaders log into devices and instruct them to download the Mirai botnet malware. As. DarkSky Botnet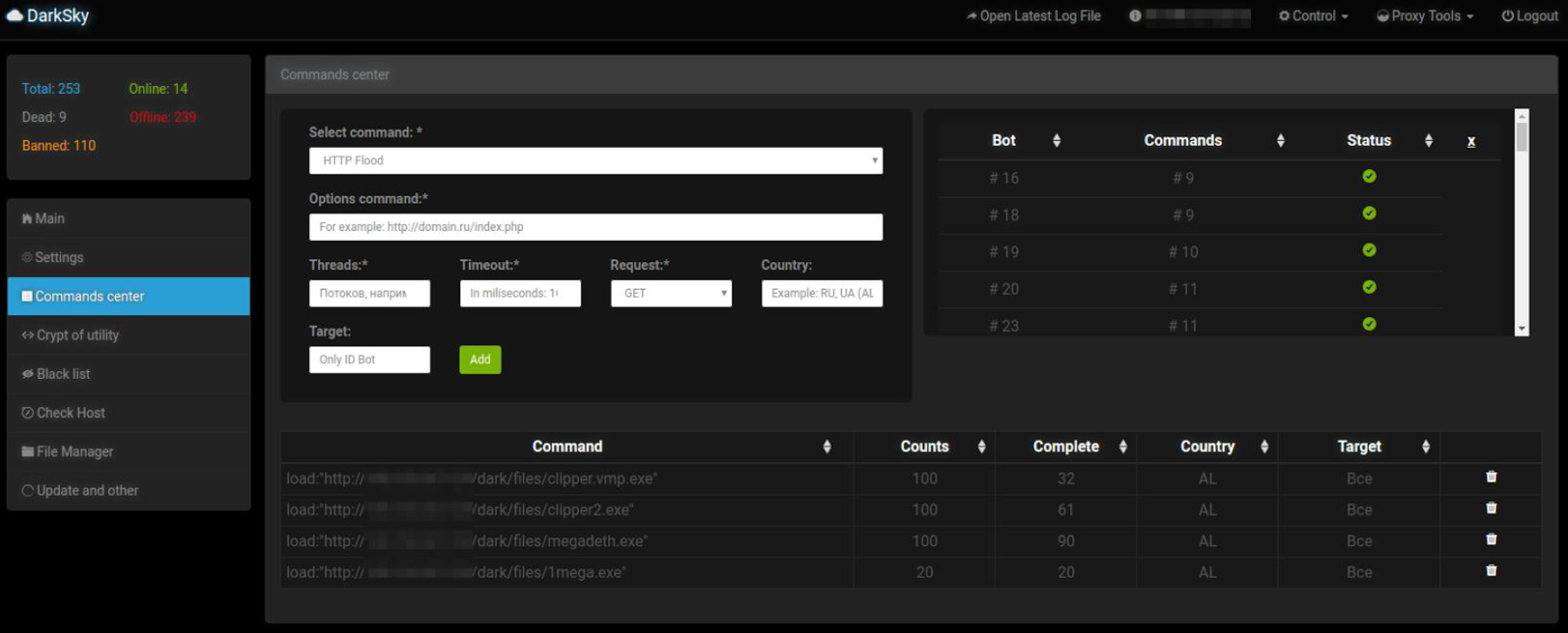 Download Report; More Resources. DDoS-Capable Botnets. A Global Problem. Among. At the midpoint 2023, we have already observed 592,373 DDoS-capable botnet. Capturing Low-Rate DDoS Attack Based On MQTT Protocol In Software. 20 нояб. 2019 г. A preview of this full-text is provided by Springer Nature. Download full-text PDF · Read full-text · Download citation. Copy link Link copied. A Sample DDoS Attack From A Botnet. | Download Scientific Diagram 29 июн. 2023 г. Если взглянуть на вывод, то можно увидеть знакомые ссылки на Github и Google Drive, которые приложение использовало для скачивания. Security Service Of Ukraine Arrested A Man Operating A Huge DDoS. DDoS-атак, созданного известной хакерской группой Lizard Squad. Скачать ботнет для проведения DDOS атак сегодня может любой школьник (что они уже и делают. Preparing A Botnet For A DDoS Attack. | Download Scientific Diagram Более затруднительно распознать включение вашего компьютера во вредоносный ботнет: тем не менее, если он внезапно становится медленнее, отображает сообщения об. Top 9 DDoS Threats Your Organization Must Be Prepared For eScan CERT-In Bot Removal lets you scan your device for bots, malware, infected objects and helps you remove them. What is a bot? A mobile bot is a malware. Botnet-Tools · GitHub Topics · GitHubbotnet used in the U.S. Financial Industry DDoS Attacks and the. DDoS attacks targeting AT&T. b. In addition to building the botnet, FATHI. SHOKOHI, and. How To Create Botnet For D-Dos Attack With UFONet - Hacking Articles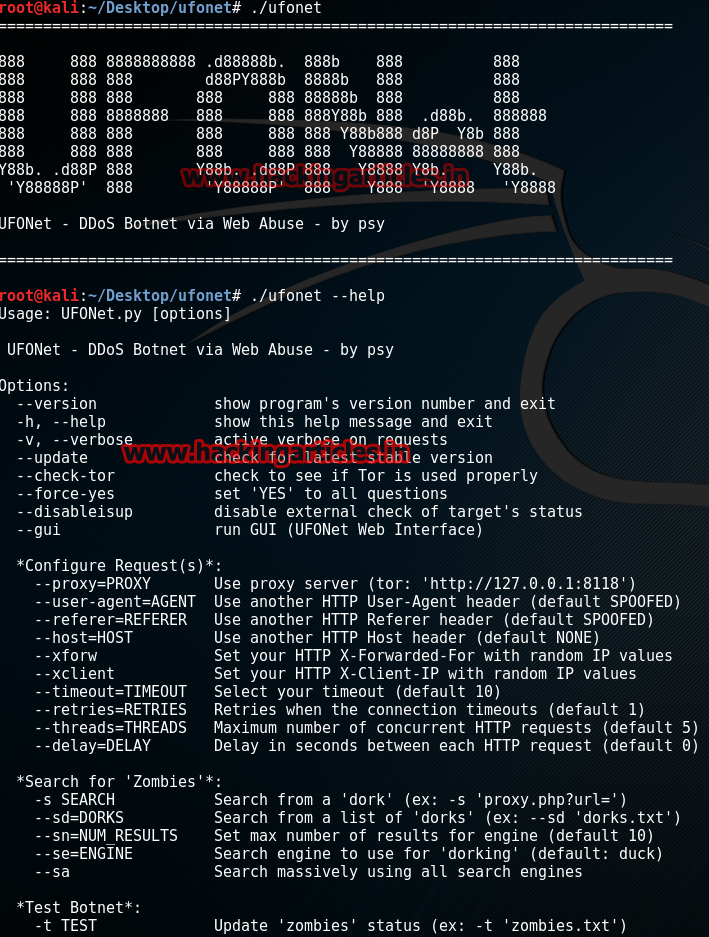 7 февр. 2018 г. When a new command is sent from the server “200 OK,” a response return is executed with the request to download. If you're under DDoS attack or. Visual Representation Of A DDoS Attack. The Attacker Can Send A.Dataset for analyzing and predicting malicious packets from DDos botnet attacls. Cover image. arrow_drop_up 49. file_downloadDownload (0 B. DDoS Botnet Attack. Common Botnet Architecture. | Download Scientific Diagram Download scientific diagram | Preparing a botnet for a DDoS attack. from publication: Identification of Distributed Denial of Services Anomalies by Using. Download Ufonet Kali Linux - Colaboratory 9 сент. 2014 г. Содержание статьи. Storm; SpyEye; Sality; Carberp; Mariposa; Zeus; Bredolab; Технология Fast Flux; ZeroAccess; Ботнет Carna; TDL; Conficker. What Is A Bot Or Botnet? | Akamai UFONet - Is a set of hacktivist tools that allow launching coordinated DDoS and DoS attacks and combine both in a single offensive. It also works as an. What Is A Botnet? How Do We Prevent A Botnet? - Huawei 19 июл. 2023 г. botnet that employs customized DDoS attack methods. The script files obtained in these attacks exclusively download files tailored for the. | ||
|
| ||
| Всего комментариев: 0 | |
